7 Key Steps of Incident Response That Protect Your Organization
Etactics
MAY 16, 2024
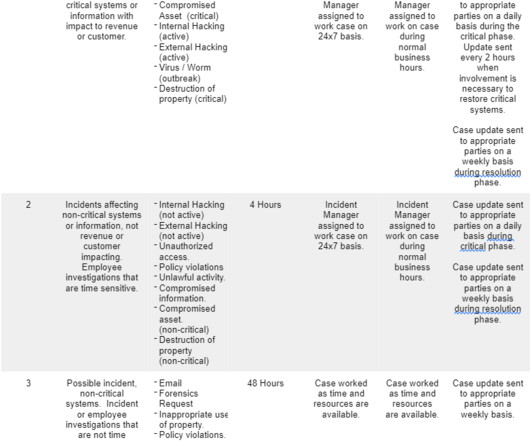
Although not a method of front-end breach prevention, incident response plans are a key component that organizations need in case they fall victim. Yet only 45% of companies have an incident response plan in place. Table of Contents What is an Incident Response Plan?





































Let's personalize your content