What is CMMC Compliance: An Authorized C3PAO Perspective
Etactics
NOVEMBER 22, 2022
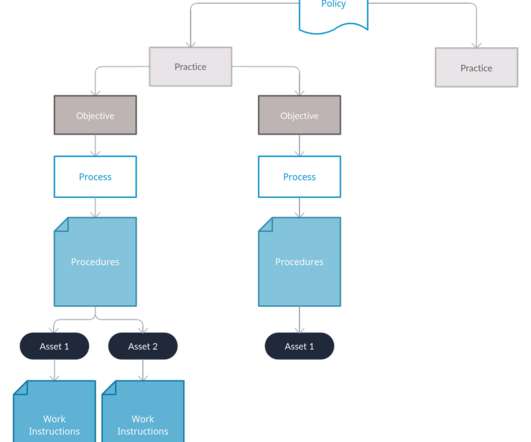
At the time of writing this blog, there are currently 29 CMMC 3rd Party Assessor Organizations (C3PAOs) listed in The Cyber AB Marketplace. These organizations have passed a third party assessment. The founders were information security assessors. About Kompleye. Kompleye formed in late 2019. The CMMC Compliance Journey.







Let's personalize your content