As organizations prepare for CMMC, the first question they need to answer is what controlled unclassified information (CUI) they have.
This will determine the scope of information systems that process, store, or transmit CUI.
In an ideal world, the government marks all CUI when it flows to contractors. As it flows down to subcontractors, it gets marked again. Sounds pretty simple.
However, anyone within the Defense Industrial Base (DIB) will tell you that identifying CUI is a significant hurdle.
The easy solution to that hurdle is just giving everything you work with this designation, right?
Well, overstating CUI significantly increases the cost for compliance across more information systems. So unless you want to take on more overhead costs, this probably isn’t the solution.
What should you do?
This blog takes a closer look at the regulations, manuals, policies, and instructions guiding CUI designation.
Table of Contents
What is CUI?
Unclassified information exists throughout the executive branch of the U.S. Government that requires any kind of safeguarding or dissemination control.
Executive Order 13556 defined CUI in November 2010 as information that law, regulation, or government-wide policy requires to have safeguarding or disseminating controls.
What isn't CUI?
CUI doesn’t include information classified under Executive Order 13526 or the Atomic Energy Act. This includes any information classified as “Top Secret”, “Secret”, or “Confidential”.
Information that a non-executive branch entity possesses that didn’t come from or wasn’t created or possessed by an executive branch agency or an entity acting on their behalf is also excluded.
CUI doesn’t include information lawfully and publicly available without restrictions. Publicly disclosed information may not be subsequently designated or redesignated CUI.
What is the relationship between CUI, CTI and CDI?
These terms often appear in different places and may cause some confusion about their relationship.
Controlled Technical Information (CTI) is a category of CUI that’s technical information with military or space application that’s subject to controls on…
Access
Use
Reproduction
Modification
Performance
Display
Release
Disclosure
Dissemination
Covered Defense Information (CDI) is CTI or other information as described in the CUI registry that requires safeguarding or disseminating controls according to…
Law
Regulations
Government-wide policies
Simply put, CDI is CUI, and CTI is a category of CUI.
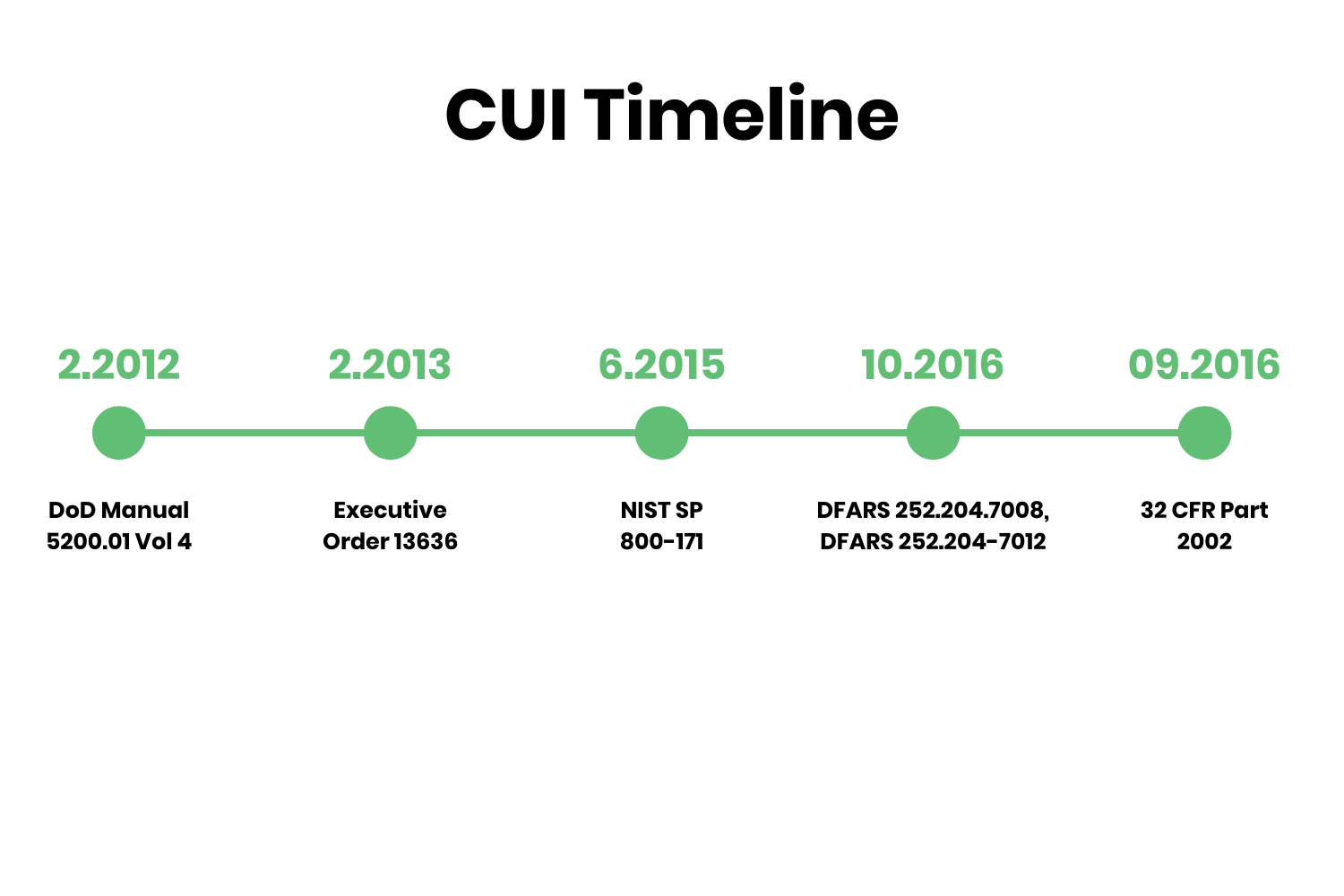
A Brief History of CUI
The DoD Manual 5200.01, Vol 4 released way back in February 2012. It’s purpose was to provide procedures for the designation, marking, protection, and dissemination of CUI.
At that time, implementation was only focused on government agencies.
Executive Order 13636 added the first private industry, Critical Infrastructure, in 2013.
NIST issued Special Publication (SP) 800-171 in 2015 to support this executive order by providing guidelines for protecting information in nonfederal systems.
By June 2016, federal contracts began requiring all contracting organizations, suppliers, and providers to meet CUI control requirements. General Services Administration (GSA) added CUI management to the Federal Acquisition Regulations (FAR) with clause 52.204-21.
In October 2016, the DoD issued the Defense version with DFARS clauses 252.204.7008 and 252.204-7012, These clauses require managing and securing CUI in accordance with NIST 800-171 and assessing those efforts using NIST SP 800-171A.
The National Archives and Records Administration (NARA) serves as the Executive Agent (EA) to implement Executive Order 13556 and oversees agency actions to ensure compliance.
In September 2016, NARA in conjunction with the Office of Management and Budget (OMB), issued 32 CFR Part 2002 for CUI management and control.
This rule affected Federal agencies and all organizations that handle, possess, use, share, or receive CUI. It also affects those that operate, use, or have access to Federal information and information systems on behalf of an agency.
Who designates CUI?
Determining whether or not information qualifies for CUI status falls on the originator.
If they do determine that it qualifies, they’re also responsible for applying the appropriate markings.
However, all of this doesn’t entirely prevent marking modifications. Officials higher in the chain of command or functional experts might also apply additional markings.
Security Classification Guide (SCG)
DFARS 252.204-7012 mandated that any DoD solicitation/contract indicates when it involves or expects to involve covered defense information.
The government marks all covered defense information provided to the contractor as CUI. This marking exists in the contract, task order, or delivery order.
The responsible original classification authority (OCA) will issue a security classification guide (SCG) for each…
System
Plan
Program
Project.
DoDM 5200.45 encourages OCAs and developers of SCGs guides to specify items or elements of unclassified information or CUI.
How is CUI designated?
Designating CUI occurs when an authorized holder determines that a specific item of information falls into a category or subcategory requiring markings and or dissemination instructions.
Authorized holders can be individuals, agencies, organizations, or a group of users permitted to designate or handle CUI.
NARA, acting as the EA, approves categories and subcategories and publishes the National CUI Registry.
Agencies may use only what’s approved by the EA. From there they put in place corresponding safeguarding or dissemination controls.
The National CUI Registry
The National CUI Registry is a catalog of information types.
There are 125 categories broken down into 20 organization index groupings...
Critical infrastructure
Defense
Export Control
Financial
Immigration
Intelligence
International Agreements
Law Enforcement
Legal
Natural and Cultural Resources
NATO
Nuclear
Patent
Privacy
Procurement and Acquisition
Proprietary Business Information
Provisional
Statistical
Tax
Transportation
The DoD CUI Registry
DoD Instruction 5200.48 from March 6, 2020, introduced the official DoD CUI Registry, which provides an official list of indexes and categories to identify CUI.
The DoD’s registry mirrors the National CUI Registry but provides more information on the relationships to DoD. It aligns each Index and Category to DoD issuances.
For example, the table below from the DoD’s registry for the defense information organizational index group shows the related categories and authorities...
| Index | CUI Categories | Category Abbreviations | Authorities |
|---|---|---|---|
| Defense | Controlled Technical Information | CTI | 48 CFR 252.204-7012 |
| Defense | DoD Critical Infrastructure Security Information | DCRIT | 10 USC 130e |
| Defense | Naval Nuclear Propulsion Information | NNPI | 42 USC 2511 |
| Defense | Naval Nuclear Propulsion Information | NNPI | 50 USC 2511 |
| Defense | Unclassified Controlled Nuclear Information - Defense (UCNI) | DCNI | 10 USC 128(a) |
| Defense | Unclassified Controlled Nuclear Information - Defense (UCNI) | DCNI | 32 CFR 223 |
Legacy Information
DoD legacy information doesn’t automatically become CUI.
For example, not all For Official Use Only (FOUO) documents to qualify. The owner of legacy documents must review the information to determine if it meets CUI requirements.
Document owners should designate any new document created with information derived from legacy material if it exists outside of the DoD.
Legacy material that remains under DoD control and within the ecosystem won’t re-receive a designation. The owner should re-mark legacy information as CUI only if it meets the requirements and the document is being shared outside DoD.
This doesn't include information stored on DoD access-controlled websites or databases.
Contractors Generating CUI
DoDI 5230.24 requires contractors to assign a distribution statement to all newly created, revised, or previously unmarked classified and unclassified DoD technical documents.
This is to prevent unauthorized recipients of this information from being able to design, engineer, produce, manufacture, operate, repair, overhaul, or reproduce any military or space equipment or technology.
This applies to technical documents generated or managed by all DoD-funded research, development, test, and evaluation programs and to newly created technical documents and other technical information...
engineering drawings
engineering data
standards
specifications
technical manuals
technical reports
technical orders
blueprints
plans
instructions
computer software
computer documentation
catalog-item identifications data sets
studies and analyses
The language found in DoDI 5230.24 closely matches Volume 4 of DoDI 5200.01 (replaced by DoDI 5200.48).
Further reading of 5200.01 tells us distribution statements aren’t intended for use on program documentation such as…
Administrative documents
Contracting documents
General correspondence
This is true unless these documents also contain technical information.
During the October 2021 CMMC-AB Town Hall, a representative from the Defense Industrial Base Cybersecurity Assessment Center, acknowledged that it takes skill to navigate the laws, regulations, and government-wide policies referenced in the CUI registry. His recommendation to contractors was to send a formal letter to their contracting officer if they are unsure information qualifies as CUI.
Examples of CUI
Is an invoice generated by a contractor working on a project involving CTI considered CUI?
An invoice is an administrative or contract document. As long as that invoice doesn’t include technical information, then DoDI 5230.24 would instruct us to not give it a designation.
Does an email from a colleague to another, who are both working on a project involving CUI, meet the designation?
An email is a general correspondence. If the contents or attachments of the email contained technical information, then the email meets the designation.
Conclusion
Now that you know how to identify what is CUI and you can filter out what isn’t CUI, the next step is to find it.
CUI may exist on servers, desktops, laptops and tablets all across your organization. Identifying all these systems that contain or have access to CUI is time-consuming.
The use of an intelligent agent may help to streamline the process of identifying where this data exists and confirming where it doesn’t.
Because these types of tools can also identify system configurations and software installed, we can also start to automate the process of gathering objective evidence and storing it into a compliance tracking solution.











![[ANSWERED] Who is Responsible for Protecting CUI?](https://images.squarespace-cdn.com/content/v1/5aa96c579772aea9adaa2ef7/1711544164425-9EUC2UOBJX2IVJSG8J26/WhoisResponsibleforProtectingCUI_324.png)





![[ANSWERED] What is CMMC 2.0?](https://images.squarespace-cdn.com/content/v1/5aa96c579772aea9adaa2ef7/1687903759952-6B6ODVEVCXXO8XGPMD3K/CMMC2.0_623.png)



Here’s everything you need to know about CMMC Level 1 continuous monitoring.